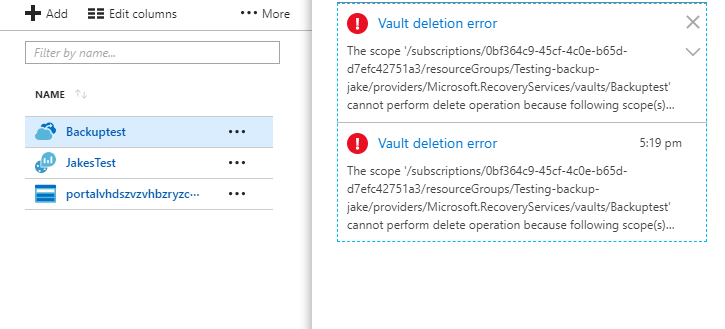
When following the steps to install the power Exchange Online Remote PowerShell Module for multi-factor authentication and you get the error that says:
Cannot Start Application
Application cannot be started. Contact the application vendor.

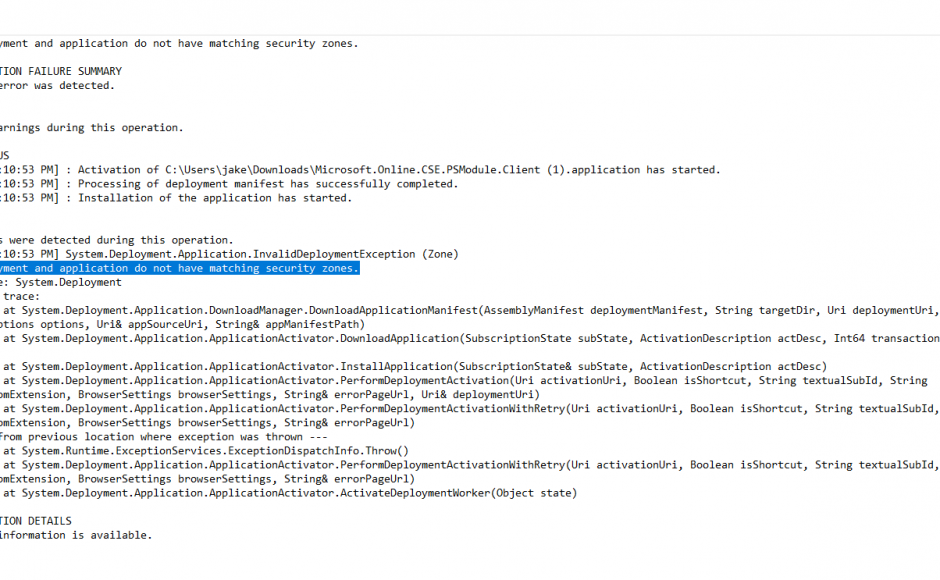
If you hit details you will get a stack trace similar to below:
PLATFORM VERSION INFO
Windows : 10.0.16299.0 (Win32NT)
Common Language Runtime : 4.0.30319.42000
System.Deployment.dll : 4.7.2556.0 built by: NET471REL1
clr.dll : 4.7.2633.0 built by: NET471REL1LAST_C
dfdll.dll : 4.7.2556.0 built by: NET471REL1
dfshim.dll : 10.0.16299.15 (WinBuild.160101.0800)
SOURCES
Deployment url : file:///C:/Users/jake/Downloads/Microsoft.Online.CSE.PSModule.Client%20(1).application
IDENTITIES
Deployment Identity : Microsoft.Online.CSE.PSModule.Client.application, Version=16.0.2186.0, Culture=neutral, PublicKeyToken=a8eee8aa09b0c4a7, processorArchitecture=msil
APPLICATION SUMMARY
* Installable application.
* Trust url parameter is set.
ERROR SUMMARY
Below is a summary of the errors, details of these errors are listed later in the log.
* Activation of C:\Users\jake\Downloads\Microsoft.Online.CSE.PSModule.Client (1).application resulted in exception. Following failure messages were detected:
+ Deployment and application do not have matching security zones.
COMPONENT STORE TRANSACTION FAILURE SUMMARY
No transaction error was detected.
WARNINGS
There were no warnings during this operation.
OPERATION PROGRESS STATUS
* [13/03/2018 8:10:53 PM] : Activation of C:\Users\jake\Downloads\Microsoft.Online.CSE.PSModule.Client (1).application has started.
* [13/03/2018 8:10:53 PM] : Processing of deployment manifest has successfully completed.
* [13/03/2018 8:10:53 PM] : Installation of the application has started.
ERROR DETAILS
Following errors were detected during this operation.
* [13/03/2018 8:10:53 PM] System.Deployment.Application.InvalidDeploymentException (Zone)
– Deployment and application do not have matching security zones.
– Source: System.Deployment
– Stack trace:
at System.Deployment.Application.DownloadManager.DownloadApplicationManifest(AssemblyManifest deploymentManifest, String targetDir, Uri deploymentUri, IDownloadNotification notification, DownloadOptions options, Uri& appSourceUri, String& appManifestPath)
at System.Deployment.Application.ApplicationActivator.DownloadApplication(SubscriptionState subState, ActivationDescription actDesc, Int64 transactionId, TempDirectory& downloadTemp)
at System.Deployment.Application.ApplicationActivator.InstallApplication(SubscriptionState& subState, ActivationDescription actDesc)
at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivation(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl, Uri& deploymentUri)
at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivationWithRetry(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl)
— End of stack trace from previous location where exception was thrown —
at System.Runtime.ExceptionServices.ExceptionDispatchInfo.Throw()
at System.Deployment.Application.ApplicationActivator.PerformDeploymentActivationWithRetry(Uri activationUri, Boolean isShortcut, String textualSubId, String deploymentProviderUrlFromExtension, BrowserSettings browserSettings, String& errorPageUrl)
at System.Deployment.Application.ApplicationActivator.ActivateDeploymentWorker(Object state)
COMPONENT STORE TRANSACTION DETAILS
No transaction information is available.
How to fix Exchange Online Remote PowerShell Module for multi-factor authentication installation issue
Download the installer from Office 365 using Internet Explorer, then when you install it works.
Not sure why you have to use IE but that is how it works for me.
Read More →