A common data breach method that I have seen on emails is leveraging client forwarding rules to forward every email received to a third party.
Basically a “hacker” will gain access into a mailbox (usually through social engineering) and then setup forwarding rules on the mailbox so all of the emails will be received by the intended recipient as well as forwarding the email to the malicious third party.
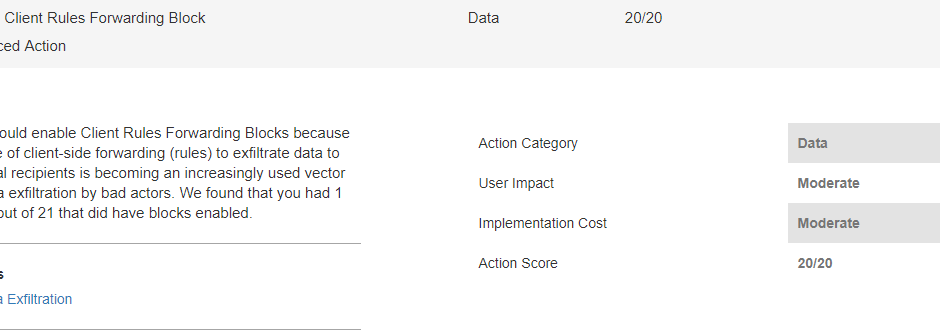
This risk can be mitigated by disabling client forwarding rules to external domains. This means that your email server will not allow auto-forwarding of emails to domains that are not part of your organisation.
How to disable client forwarding rules to external domains in office 365 or Exchange Server
If you have an enterprise SKU of Office 365 you can use the secure score function to automatically create the rule, just go to https://securescore.office.com/ and enable Client Forwarding Rules Block.
Manually setting a rule to block autoforwarding
If you do not have an enterprise SKU on office 365 (or if you have an on premise exchange server) you will need to manually create the mail flow rule to block auto forward emails.
You will need to go to the exchange admin center an under rules select new rule & then follow the video above that has the instructions on setting up the rule.
Some other useful informaiton around securing your email environment:
How to Setup Outbound Spam notifications on Office 365 or Exchange